When it comes to free cybersecurity resources, you can’t get much better than MITRE ATT&CK.
This globally-accessible knowledge base details the methods and means that threat actors deploy to attack their targets — providing the reader with tremendous insights into how threat actors operate. It’s no surprise, then, that cybersecurity professionals find MITRE ATT&CK exceptionally useful, as the below tweet illustrates.

Think about it this way, we need to have frameworks and tools which can be used to better understand the TTPs (Tactics Techniques and Procedures) of threat actors, in order to allow us to build a better understanding of how to protect ourselves. Similar to the methods in military conflict, cyber attackers plan their attacks, using well defined approaches to breaching our defenses. As a result, it becomes clear that we need tools to understand the way in which attackers act, in order to help us to build better defenses.
So how can you put MITRE ATT&CK to use?
MITRE ATT&CK explained
MITRE ATT&CK was developed to stop threat actors from carrying out offensives, specifically those that were damaging and inhibiting the operations of systems such as Microsoft Windows.
Its scope has since spread to incorporate macOS and Linux devices as well as network and cloud. In fact, the scope is the entire enterprise infrastructure now, as well as mobile and Industrial Control Systems (ICS) - essentially OT.
But what is MITRE ATT&CK exactly? Put simply, it’s a curated body of work that’s characterized by matrices. These matrices are informed by an encyclopedic array of historical actions and tactics used by threat actors, culminating in an actionable framework to follow for managing cybersecurity issues.
Crucially, MITRE ATT&CK is built on the belief that viewing your security set-up through the eyes of an attacker is the most effective strategy. It’s this premise that makes MITRE ATT&CK such a valuable resource for unearthing the vulnerabilities that are built into your system.
By using MITRE ATT&CK, you’ll gain greater clarity when analyzing your weak spots. Knowing how to break through your own defenses makes you aware of the methods that are likely to be used against you.
The MITRE Corporation has also brought the industry several other tools including CAPEC™ and CWE™, both of which are specifically focused on unveiling methodologies employed by threat actors.
MITRE ATT&CK background and history
MITRE’s research department, FMX, created the ATT&CK taxonomy as a way of categorizing and laying out the behavior displayed by threat actors. This enabled the research team to run imitation exercises in order to better understand the dynamics of attacks and, consequently, respond to them with greater efficacy.
MITRE ATT&CK has been continuously developed over a series of evolutionary stages, either in response to demand for device compatibility and/or the ever-changing landscape of cybersecurity.
Understanding key ATT&CK terminology
You’ll see the words ‘tactics’, ‘techniques’, and ‘procedures’ used a lot in MITRE frameworks and output. These key terms are defined as:
- Tactics - The umbrella word for the different methods that attackers utilize when carrying out malicious actions.
- Techniques - Ways that an adversary carries out their desired tactics. An example would be Phishing (technique) as a vector to obtain primary access (tactic) to begin their attack.
- Procedures - Specific techniques and tools that are deployed by threat actors.
How to use MITRE ATT&CK
The most recent version of ATT&CK covers 14 tactics that threat actors utilize:
| Reconnaissance | The adversary is trying to gather information they can use to plan future operations. |
| Resource Development | The threat actor is trying to establish resources they can use to support operations. |
| Initial Access | The threat actor is trying to get into your network. |
| Execution | The threat actor is trying to run malicious code. |
| Persistence | The threat actor is trying to maintain their foothold. |
| Privilege Escalation | The threat actor is trying to gain higher-level permissions. |
| Defense Evasion | The threat actor is trying to avoid being detected. |
| Credential Access | The threat actor is trying to steal account names and passwords. |
| Discovery | The threat actor is trying to figure out your environment. |
| Lateral Movement | The threat actor is trying to move through your environment. |
| Collection | The threat actor is trying to gather data of interest to their goal. |
| Command and Control | The threat actor is trying to communicate with compromised systems to control them. |
| Exfiltration | The threat actor is trying to steal data. |
| Impact | The threat actor is trying to manipulate, interrupt, or destroy your systems and data. |
Recognizing the different tactics is important because understanding a threat actor's goals and methods will allow for better prep and prevention tactics. Additionally, under each tactic, ATT&CK goes on to list a number of techniques that can be used in executing that tactic.
In the example of penetration testing: penetration will typically cover tactics such as reconnaissance and initial access. The techniques listed by ATT&CK for those tactics provide guidelines to understand what would need to be covered in a penetration test.
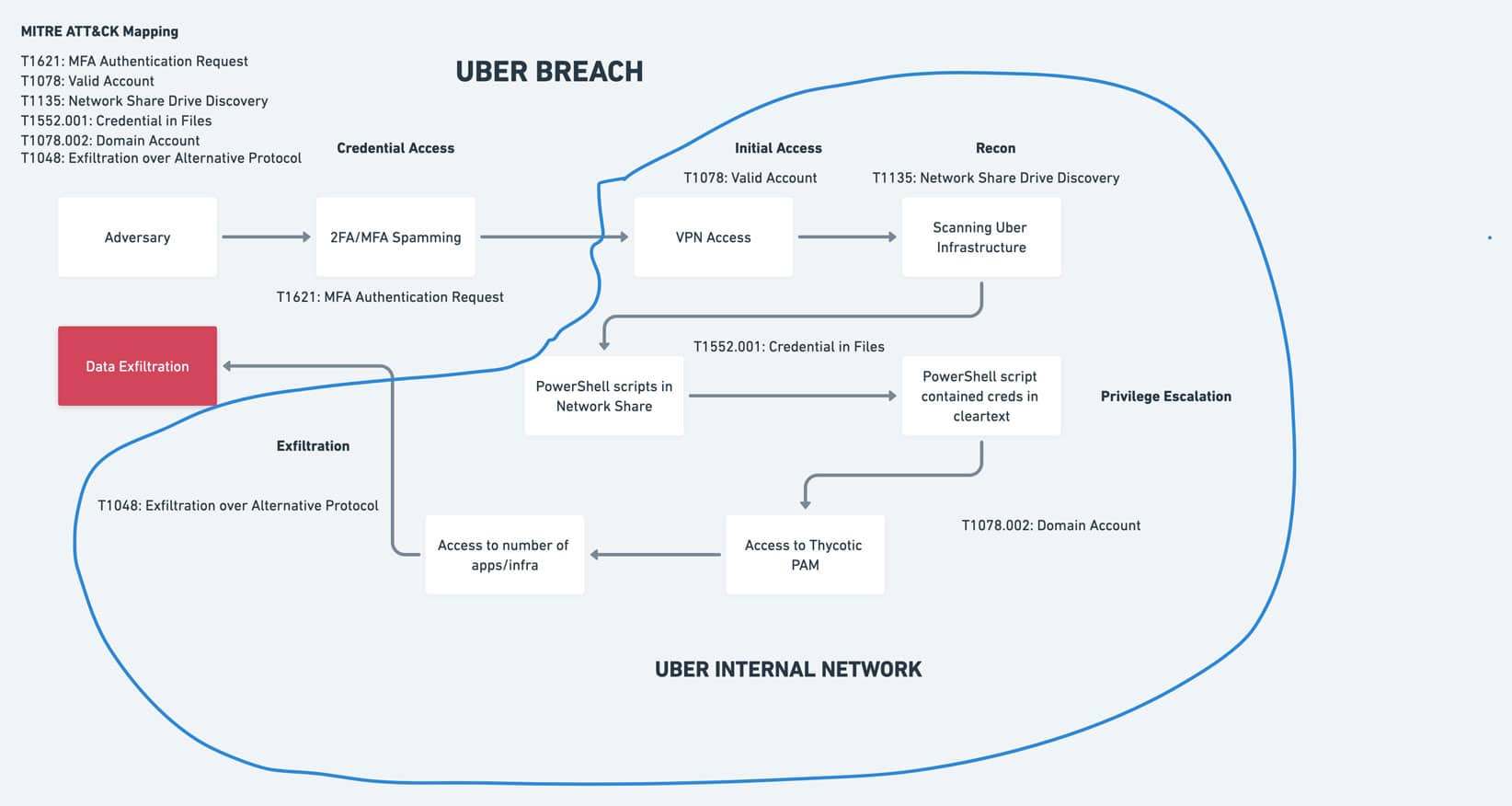
Here is a mapping that was done of the recent Uber breach to the MITRE ATT&CK framework. This mapping also illustrates how MITRE ATT&CK helps us understand the process followed by the attacker. Unfortunately this particular breach was not discovered until it was completed. Had the attack been discovered during one of its earlier stages, MITRE ATT&CK would have helped defenders to predict the next steps the attacker might take, providing insights on how to focus response activities.
There are several uses for the framework, including:
Improving threat identification
The MITRE ATT&CK framework utilizes data outlets that include event and authentication logs and file and registry monitoring, amongst other similar sources.
When this information is collated and stockpiled, analysis of the logged data can then be used to inform cybersecurity practice.
MITRE ATT&CK’s ‘Technical Information Gathering’ is put to work within Samurai’s cybersecurity UI. Here, the framework is beneficial for analyzing blocked connections and determining the source of the issue, such as an IP server.
Designing of penetration tests
Penetration testing can be used to determine the effectiveness of your cybersecurity approach. It often follows these steps:
- Use the ATT&CK methodology to select a technique and deploy analytics within your system.
- Use Atomic Red Team (or other security test providers) to test for your chosen technique.
- Carry out the test to highlight anomalies and then examine any notable findings.
- Make use of feedback from the test to inform your cybersecurity process going forward.
Coverage assessment
Cybersecurity teams can map and compare their approach to the ATT&CK framework to deduce what’s missing — or see how much coverage they have.
This is a helpful way to inform your methodology of where your blind spots are or what kind of attacks you may be susceptible to.
MITRE ATT&CK vs Lockheed Martin Cyber Kill Chain
At face value, MITRE ATT&CK could be seen as similar to Lockheed Cyber Kill Chain. After all, they both map out a similar attack structure (a threat actor first gains access, then tries to evade identification while harvesting information).
But the two are actually very different.
- Lockheed Cyber Kill Chain proposes a linear progression sequence of events. It utilizes a military kill chain concept to catch the threat actor and eliminate the danger at one of the specific steps.
- MITRE ATT&CK reflects a matrix of pathways that adversaries take, as opposed to a single sequence. It offers a deep knowledge base with environment-specific information that’s far closer to real-world attacks.
When to use MITRE ATT&CK vs Lockheed Martin Cyber Kill Chain?
- Cyber Kill Chain can be a helpful tool for understanding a specific high-level threat and following the sequence order of their offensive.
- The MITRE ATT&CK matrices, on the other hand, enable users to anticipate threats thanks to an understanding of the various options that an adversary looks to utilize.
Both methods are effective in their own ways; you apply one or both tools, depending on your objectives. In fact, when used in tandem, the two deliver a framework that’s highly effective at safeguarding cybersecurity.
Speak to Samurai about your cybersecurity needs
At Samurai, we build our cybersecurity on top-quality contextual information from across the cyber landscape. MITRE ATT&CK is just one example of the resources that we use to inform our processes to keep your enterprise safe.
We process over 800 billion logs per month — so get in touch today to safeguard your system with Samurai.
Featured articles
Identity Management in the Physical and Digital Worlds
7 August 2024 | Webinars
In today's rapidly evolving world, managing identities securely and efficiently is more crucial than ever. Join us for an insightful...
Identity Management in the Physical and Digital Worlds
30 July 2024 | Webinars
In today's rapidly evolving world, managing identities securely and efficiently is more crucial than ever. Join us for an insightful...
XDR for Small and Medium Businesses: Is It Worth It?
24 July 2024 | XDR
Cybersecurity is of paramount importance to virtually all organizations and SMBs have to address several specific challenges. The failure to...





