In the 2023 Global Threat Intelligence Report, we highlighted the continued increase in attacks targeting critical infrastructure and supply chains. A key sector in the supply chain for most organizations is Technology – comprised of industries such as information technology, security providers and software – which has been the most attacked sector in our customer data for the past several years, accounting for 25.9% of attacks observed in 2022.
With nearly all organizations shifting at least parts of their business or infrastructure toward cloud services, Software-as-a-Service (SaaS) is becoming an integral part of day-to-day operations and the global marketplace. According to a report by Gartner, “Worldwide public cloud services are forecast to grow 20.2% in current U.S. dollars (20.1% in constant currency) in 2023. Strong growth will continue throughout the forecast, with end-user spending exceeding $1.1 trillion U.S. dollars in 2027, a five-year CAGR of 19.6% (18.9% in constant currency).” (Forecast: Public Cloud Services, Worldwide, 2021-2027, 2Q23 Update )
As highlighted in the graphic below from Microsoft regarding shared responsibilities, there are many benefits in shifting toward cloud hosting and ‘-as-a-Service’ offerings. Some of the largest gains are in traditional data center cost savings, scalability and reduced staff requirements and efforts dependent on how much of the infrastructure, platforms and software is moved to the provider.
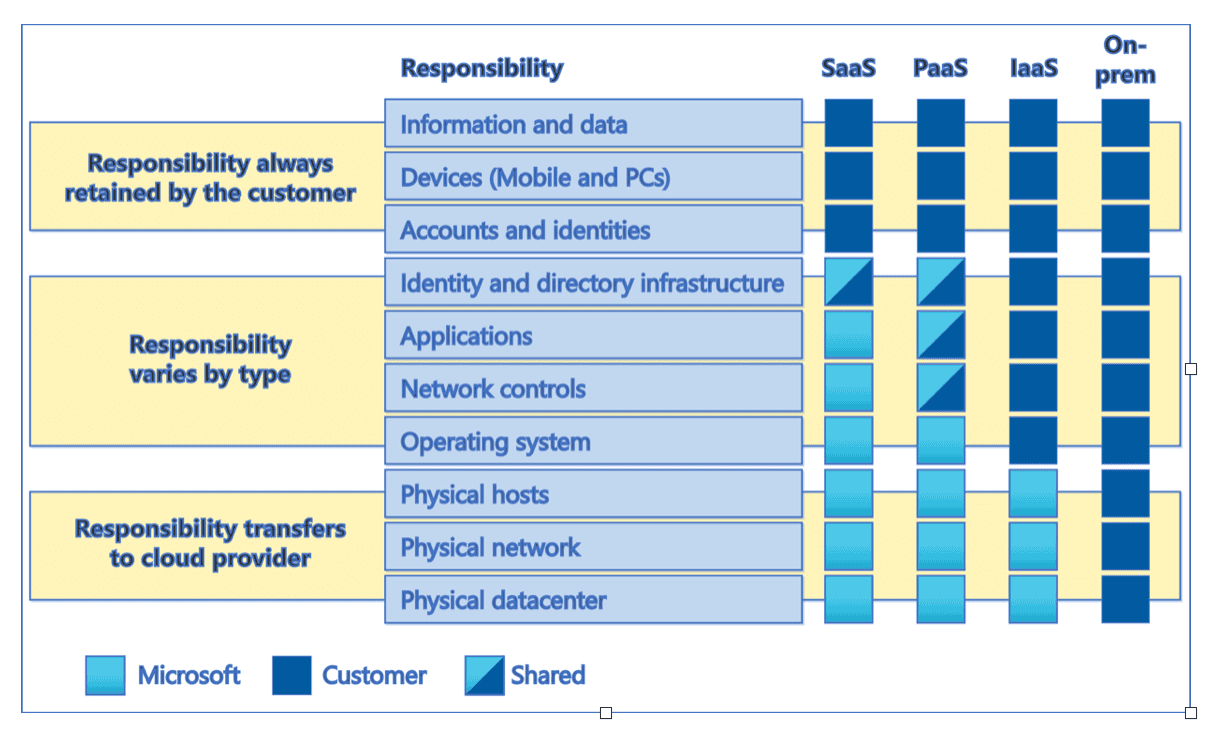 From Shared responsibility in the cloud - Microsoft Azure
From Shared responsibility in the cloud - Microsoft Azure
One of the fuzzy areas here though is information security. While much of the responsibility for data and access is maintained by the customer, this is not as clear of a split as it is often depicted. Complex vendor documentation, required add-on features, and lack of transparency can turn a very simple implementation into a juicy target for attackers. Organizations need to assess the security of the vendor themselves but also their own deployments to ensure it adheres to internal policy and controls.
Another key area of note as customers shift toward cloud hosting and SaaS providers is compliance and regulatory standards. When evaluating and selecting vendors, it is critical to ensure they have proper controls around security, availability, confidentiality, and integrity. Customers should ensure vendors are SOC 2 compliant or similar, depending on their data storage and processing needs. It is also important to note the distinction in roles and responsibilities with regulations such as the General Data Protection Regulation (GDPR). Depending on the services and data storage options involved, the vendor is often the data processor while the company remains the data controller in this setup and must adhere to those GDPR requirements.
When originally discussing the topic for this blog I intended to provide an overview from a vulnerability perspective, covering the statistics and trends around SaaS vulnerabilities and exploits in general. While collecting data from the NIST National Vulnerability Database, that highlighted another unique gap in this space. Out of over 86,000 CVEs listed since 2020, less than 200 even reference ‘SaaS’ or ‘-as-a-Service’ at all. CVEs really aren’t tracked or scored in a way that directly applies to many hosted offerings and gives an unfair feeling of protection and security.
If we look at a handful of notable breaches for SaaS or integrated cloud services in the past year, the majority didn’t in fact require any exploit code at all.
- LastPass – Valid employee credentials and keys used to access third-party cloud-based storage
- PayPal – Credential stuffing attack allowed access to user data
- ChatGPT – Exploitation of a third-party open-source library
- AT&T – Access to Customer Proprietary Network Information gained through vendor systems
- Salesforce – Misconfiguration that allowed unauthenticated user access to customer data
- Dragos – Compromised personal email of new employee, allowing limited access to ‘general use data’ in SharePoint
- MOVEit – Exploitation of critical SQL injection vulnerability in web application
- Okta (Sept) – Social engineering of super administration accounts
- Okta (Oct) – Stolen credentials for case support management system, resulting in suspicious activity of customers such as 1Password
- Microsoft Cloud – Forged authentication tokens to access multiple organizations
Based on just these ten examples, you can further see why there is a gap between the low number of SaaS vulnerability disclosures and the high number of breaches and impacted customers. In most of these cases, the breach or data leak was a result of a customer or vendor/supply chain breakdown as opposed to a 0-day or vulnerability in the hosted software, infrastructure, or security controls themselves. Expect this gap to continue, with Gartner projecting that by 2025 “99% of cloud security failures will be the customer’s fault.” (Is The Cloud Secure )
Customers put a lot of faith in these providers and are not always met with simplicity and transparency. It is also true that many of the incidents that expose customer data or simply open them up to more risk are not as straightforward as traditional vulnerabilities that are being exploited. They are more often human or implementation weaknesses, which actors understand and are more aggressively taking advantage of.
When looking at the state of SaaS security over, I’d like to leave vendors and customers with a few considerations.
Reflections for vendors based on high profile breaches:
- Eliminate Add On Fees – Where feasible, eliminate charging for key security features such as single sign on (SSO) or the logging necessary to conduct threat hunting or breach validation. In some cases there is a necessary cost that must be passed along to customers but this should ideally be a last resort.
- Reduce Complexity – Simplify documentation or at minimum, highlight critical areas and prioritize security features. It is important that vendors help ensure customer success and security to reduce exposure for all involved.
- Increase Transparency – Improvement is needed in vulnerability disclosures to account for this space and the gaps with CVE. Notate when the SaaS version of a product or agent is not vulnerable and if they ever were. While security researchers and bug bounty programs often give vendors lead time to patch before 0days or exploit code become available, this gap can lull customers into a false sense of historical security.
- Improved Segmentation – Compromise of a single set of credentials should not result in access to tens or hundreds of customers’ data. It is important that we aim to continue improving client data segmentation/microsegmentation and minimize internal access to these resources to help reduce exposure in the event of an incident.
Guidance to customers when evaluating and implementing vendors:
- Assess Provider Compliance and Security – Customers need to ensure they assess SaaS provider security throughout the vendor lifecycle, not just in the RFP or negotiation stages. Request the vendors third-party tech stack or any vendors which would have access to your data or might support your account. Ensure consistent regulatory and compliance adherence for the duration of the service.
- Improved Staff Training – Security training is a common recommendation; however it should extend beyond basic phishing knowledge. Employees need an understanding around credential security, the risks to the organization of password re-use and multi-factor authentication (MFA) threats that could now target their personal email and devices. This is becoming especially true for service desk and support users, who are being targeted at a higher rate by aggressive actors.
- Implement Phishing Resistant MFA – The rise in threat actors targeting employees with advanced phishing techniques requires more security than basic multi-factor authentication often provides. Look into alternatives to SMS or voice MFA which are easy targets and ensure employees with elevated access are aware of signs of attacks such as push bombing or SIM swapping.
This is a space that shows no signs of slowing down – both in terms of growth and breaches. It is critical for customers and vendors alike to consider security from the onset, evaluate and scope properly, and assess the security of the solution and implementation continuously. It is shortsighted to set and forget – configurations and settings change, new features are added, and failures exist just like in any IT environment.
Featured articles
Identity Management in the Physical and Digital Worlds
7 August 2024 | Webinars
In today's rapidly evolving world, managing identities securely and efficiently is more crucial than ever. Join us for an insightful...
Identity Management in the Physical and Digital Worlds
30 July 2024 | Webinars
In today's rapidly evolving world, managing identities securely and efficiently is more crucial than ever. Join us for an insightful...
XDR for Small and Medium Businesses: Is It Worth It?
24 July 2024 | XDR
Cybersecurity is of paramount importance to virtually all organizations and SMBs have to address several specific challenges. The failure to...





